-
Credential Stuffing vs Password Spraying
29. October 2020
We use Office 365 in a regular basis in my company. Don’t get me wrong – I’m hardly what you’d call a Microsoft advocate. In fact, my friends and colleagues know me rather as an Apple-fanboy and BSD-Geek. But I have to admit that Office 365 works pretty well. And, in these pandemic times when we work from home, Teams and other MS products come in very handy. As part of my company’s security team we also encounter attacks against our user accounts.…

-
AuthN vs AuthZ
23. October 2020
When you do some “login stuff” nowadays you may stumble upon the terms AuthN and AuthZ. Maybe you have wondered what the letters “N” and “Z” mean? The short answer: AuthN stands for Authentication, and AuthZ stands for Authorization. That’s easy right? I guess we’re done for this blog post 🙃 Authentication vs. Authorization But what is the difference between these two terms? Are they not the same? The short answer: No, they aren’t!…

-
OAuth 2.0 Implicit Flow Considered Harmful
8. October 2020
Certainly I’m not the only one writing into the web that OAuth 2.0 Implicit Flow is bad for security reasons and deprecated by OAuth 2.0 Best Current Practices and OAuth 2.1. But this can’t be said enough times. So I’ll try my best! This post is a guide for people facing situations where random dudes asking “Why should I bother? See, Microsoft is recommending it!” After reading this post you can tell them why it is a bad idea to use implicit flow.…

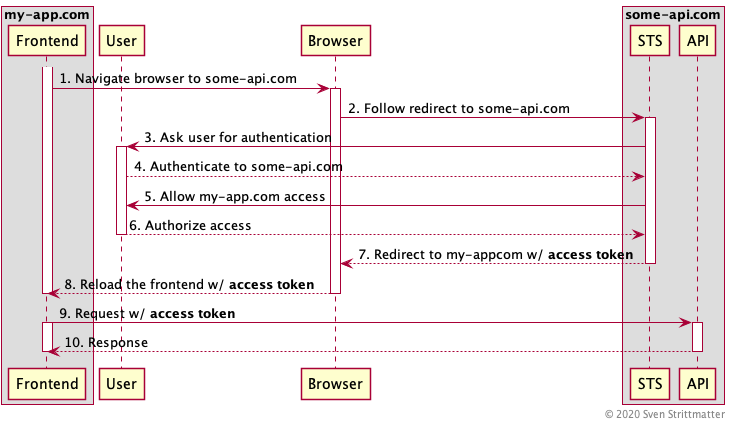
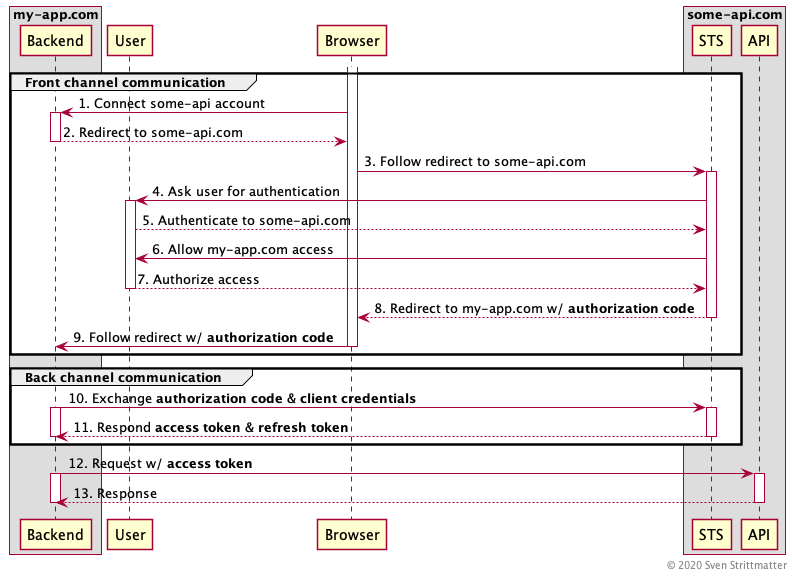
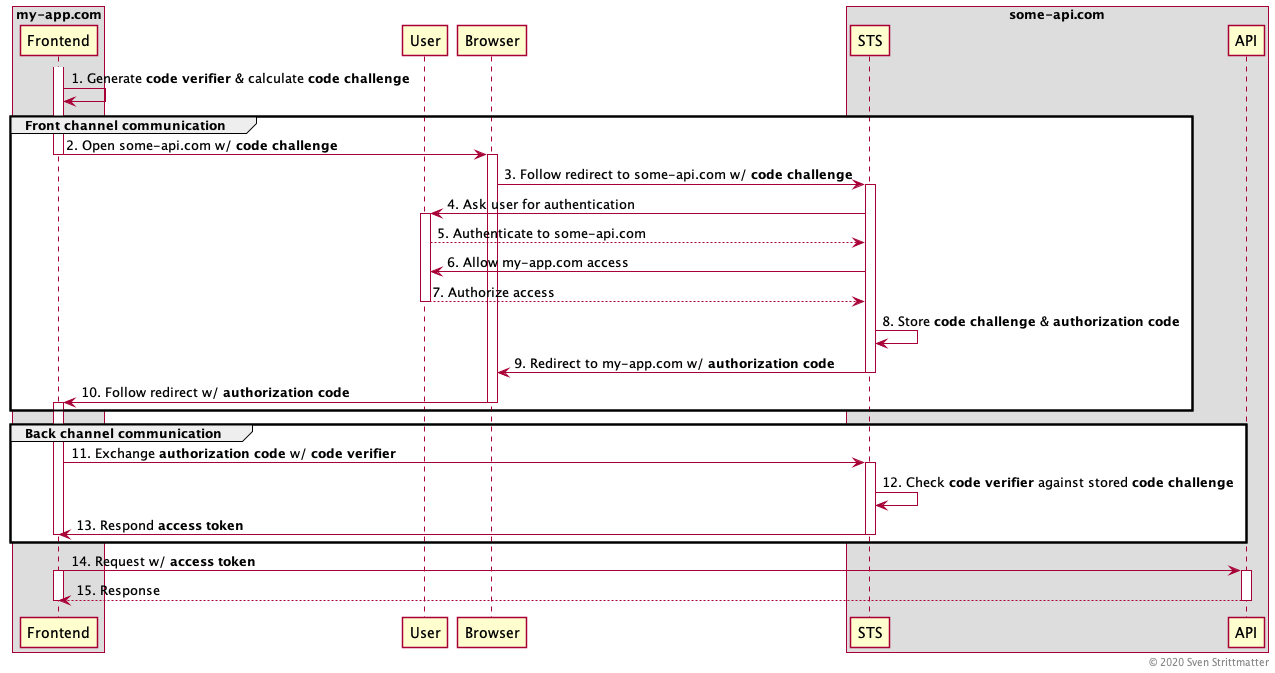
-
My Opinion on Zoom
15. May 2020
TL;DR: Do not use Zoom at all! If you have to: Use it on iOS or in the browser. Nowadays we use lots of video conferencing to practice physical distancing. A major player in the field is Zoom. One reason for that is the fact that they have a good software quality. At least on the surface it looks like they have. Because the inner software quality seems not that good.…
-
Hardening Your SSHd With Ansible
8. May 2020
Disclaimer: This is not a beginner tutorial. You should have a brief understanding and some experiences with Linux and Ansible. Whenever you run a server in the wild wild web you should harden your SSHd setup. If you wonder why you should do that, then spin up a machine with enabled SSHd and watch the logs: Usually it takes only few minutes until the first scans and brute force attacks showing up in the logs.…
-
Only SSL access to my blog
30. December 2011
Some time ago I configured my blog to serve both HTTP and HTTPS. From now on I will redirect all non-SSL requests permanently to HTTPS. The reason is that no one access the login page without SSL by accident. If you encounter any problems please let me know. Unless you have installed the CAcert root certificates in your browser, you will become a warning about my server’s certificate. To prevent this install the root certificates from here.…
-
Plugins To Harden Your WordPress
28. December 2011
Just stumbled over a blog post with a collection of 16 WordPress plugins to secure your blog installation. Some of them sounds not that strong but some of them sounds interesting. I’ll checkout some of them an maybe report about them, if they are worth mentioning it.
Security / Software Architecture / Clean Code