-
Project Libre Cloud Poor Man Style
27. April 2022
Disclaimer: The solution presented here is macOS only! Some weeksago we encountered the need for some project management tool in my team at my employer. We’re a central security team providing services to our project teams and customers. The last months we saw more and more demand for our services and we’re faced a quite complex situation. We need to allocate the team members to some small projects (like threat modelings or a security training) or larger projects (like implementing secureCodeBox in a project or consulting a customer to build their own security community).…

-
Credential Stuffing vs Password Spraying
29. October 2020
We use Office 365 in a regular basis in my company. Don’t get me wrong – I’m hardly what you’d call a Microsoft advocate. In fact, my friends and colleagues know me rather as an Apple-fanboy and BSD-Geek. But I have to admit that Office 365 works pretty well. And, in these pandemic times when we work from home, Teams and other MS products come in very handy. As part of my company’s security team we also encounter attacks against our user accounts.…

-
AuthN vs AuthZ
23. October 2020
When you do some “login stuff” nowadays you may stumble upon the terms AuthN and AuthZ. Maybe you have wondered what the letters “N” and “Z” mean? The short answer: AuthN stands for Authentication, and AuthZ stands for Authorization. That’s easy right? I guess we’re done for this blog post 🙃 Authentication vs. Authorization But what is the difference between these two terms? Are they not the same? The short answer: No, they aren’t!…

-
OAuth 2.0 Implicit Flow Considered Harmful
8. October 2020
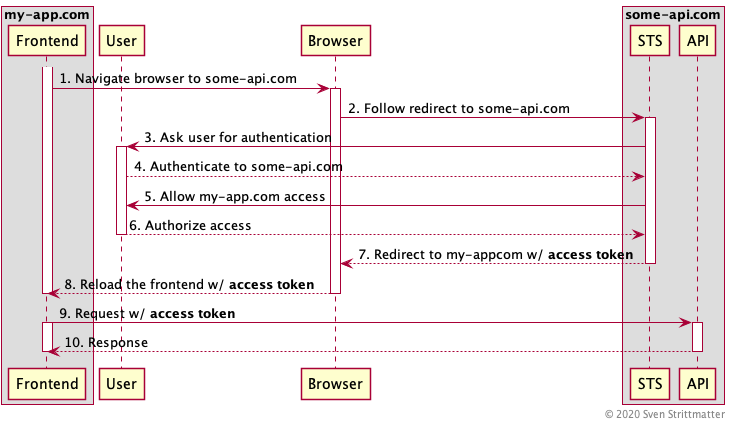
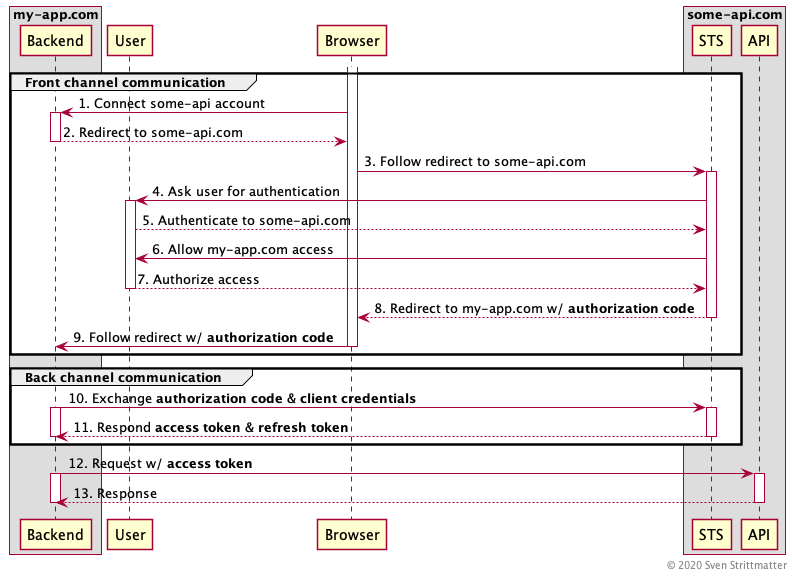
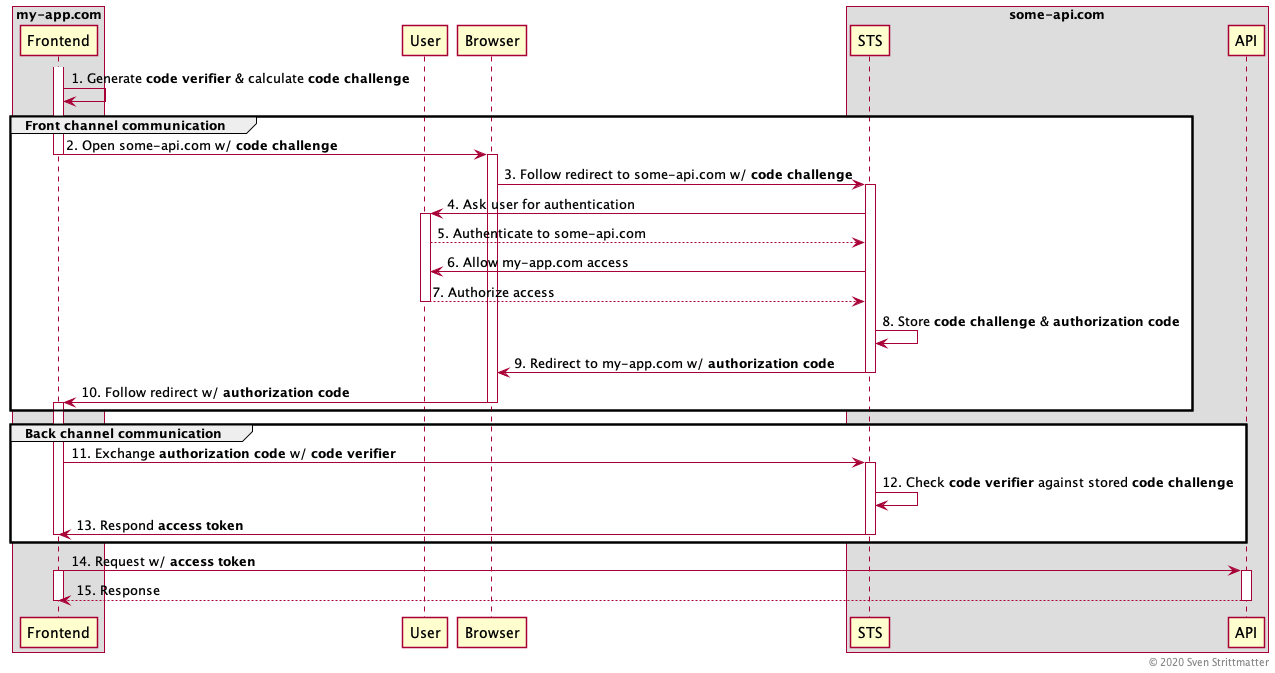
Certainly I’m not the only one writing into the web that OAuth 2.0 Implicit Flow is bad for security reasons and deprecated by OAuth 2.0 Best Current Practices and OAuth 2.1. But this can’t be said enough times. So I’ll try my best! This post is a guide for people facing situations where random dudes asking “Why should I bother? See, Microsoft is recommending it!” After reading this post you can tell them why it is a bad idea to use implicit flow.…

-
Improve Your Documentation With Russian Roulette
21. September 2020
As software dudes we write documentation. Of course we do. Most of the time we write some API docs (JavaDoc or such) in the source code. This is not a big deal in my opinion. You do this as well as writing code and tests. Also you review this regularly within the normal code reviews. Yeah, code reviews are something normal in my world! But some times we’re urged to write some documentation outside of the source code.…
-
Hide and Seek in TXT Records
18. September 2020
Did you ever wondered how the “bad guys” cover things? Some time ago John Ferrell wrote about how to hide malicious code in files looking like a good old plain text log file. Last month (August 2020) John Hammond wrote a part two. In this part he’s showing how they download additional payloads from the internet under the radar. It’s quite simple, if you know. What’s the Problem with Payloads So if you are writing malware you face the same problem as any software developer: You want to ship updates.…
-
Frauenquote
29. May 2020
Disclaimer: Ich bin ein Mann und eigentlich sollten wir Männer bei diesem Thema gepflegt die Fresse halten, weil wir nicht betroffen sind! Warum schreibe ich jetzt trotzdem etwas dazu? Letztens hat mein Arbeitskollege Stefan Rauch über das Thema Frauenquote geschrieben. Woraufhin ich kommentierte dass es meiner Meinung nach nur mit Quote gehen wird: Leider funktioniert es nur mit Quote. Das zeigt ja schon alleine wie wenig sich in den letzten Jahrzehnten getan hat.…
MiscellaneousQuoteFrauenquoteDiversitätGleichberechtigungEmanzipationFeminismus
-
Please Use Semantic Versioning
22. May 2020
TL;DR Please use Semantic Versioning and please use it right! This is a little rant about tools, libs and frameworks not using Semantic Versioning. This morning I was triggered on Twitter by the announcement of Terraform version 0.13. My first thought was: WTF! Why are you still at 0.x with a software widely used in production? Disclaimer: I use Terraform by my self and I like it. Scrolling through my time line I saw various other announcements like 0.…
-
My Opinion on Zoom
15. May 2020
TL;DR: Do not use Zoom at all! If you have to: Use it on iOS or in the browser. Nowadays we use lots of video conferencing to practice physical distancing. A major player in the field is Zoom. One reason for that is the fact that they have a good software quality. At least on the surface it looks like they have. Because the inner software quality seems not that good.…
-
Hardening Your SSHd With Ansible
8. May 2020
Disclaimer: This is not a beginner tutorial. You should have a brief understanding and some experiences with Linux and Ansible. Whenever you run a server in the wild wild web you should harden your SSHd setup. If you wonder why you should do that, then spin up a machine with enabled SSHd and watch the logs: Usually it takes only few minutes until the first scans and brute force attacks showing up in the logs.…
Security / Software Architecture / Clean Code